Phishing Example: Fake Account Deletion Notice
This example shows a normal-looking email that tries to trick users into thinking their account will be deleted unless they enter login credentials and complete multi-factor verification. If a user submits those credentials, their account can be compromised — notify Action Target IT IMMEDIATELY.
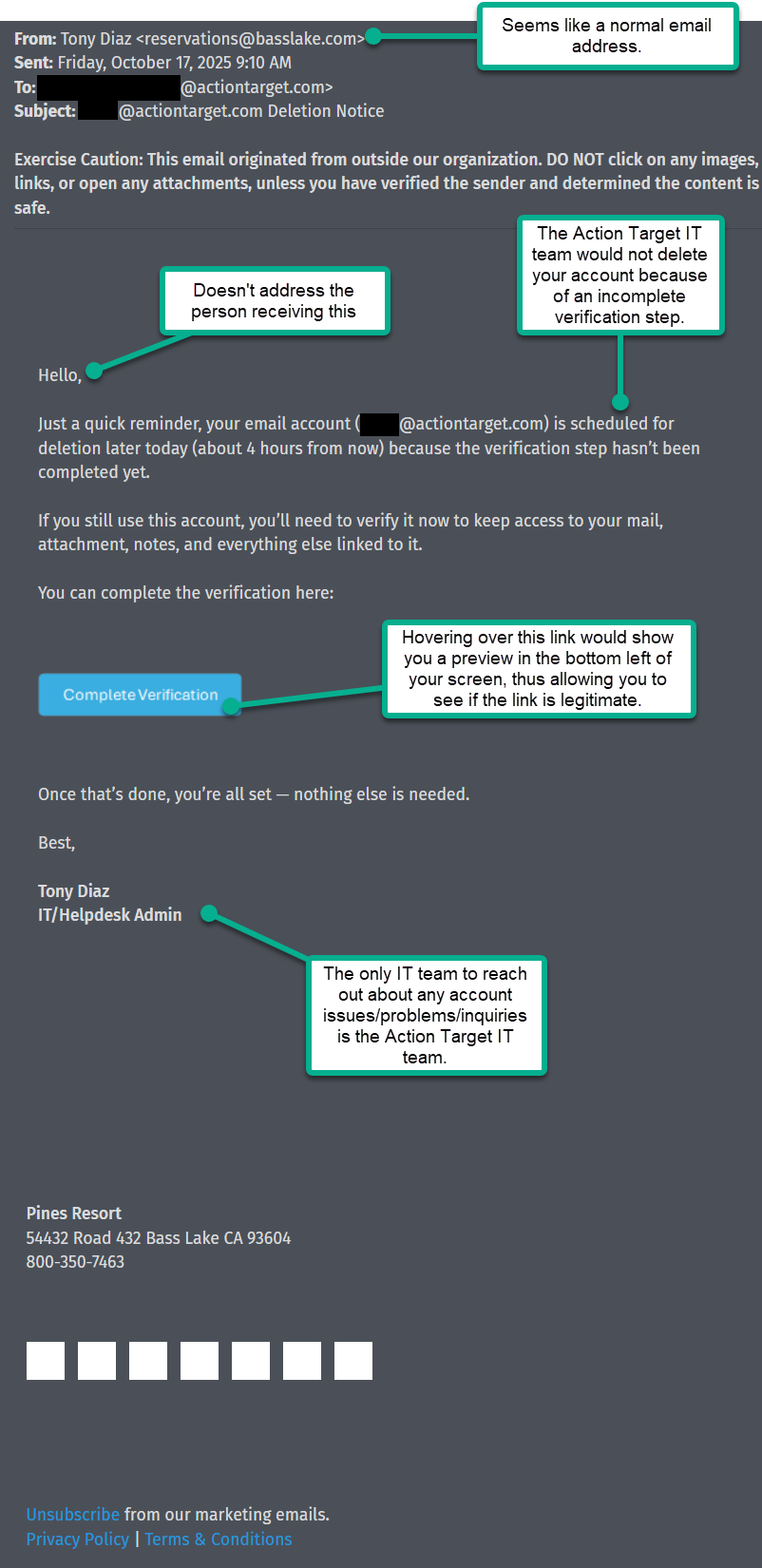
Picture #1 - The Phishing Email
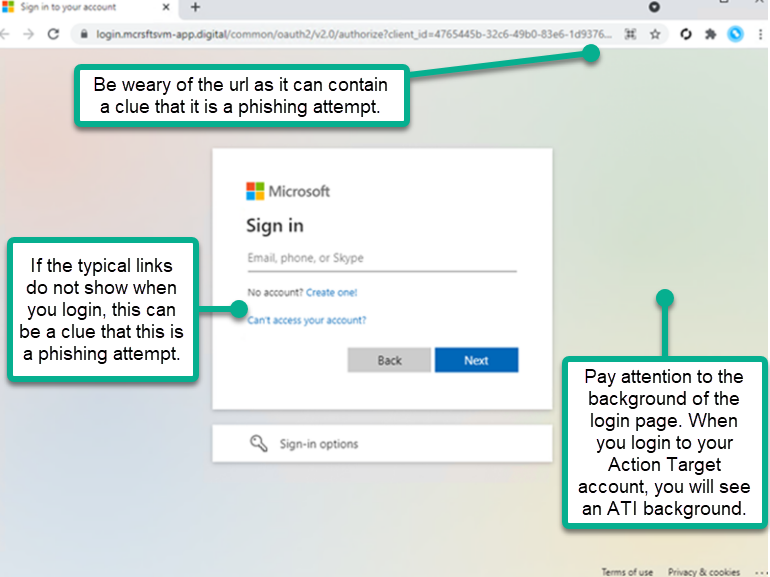
Picture #2 - Example of What You Could See by Clicking the Link
How to Verify Safely
- Hover over the link and it will show in the bottom left hand corner of the screen.
- Compare the domain against the official login domain (@actiontarget.com or company SSO URL)
- If you are unsure, open a browser and navigate manually to the company portal (do NOT click the suspicious link)
- Contact the IT team via an independent channel (phone, email, teams, ticket, in-person)
If You Clicked or Entered Credentials (URGENT)
- IMMEDIATELY notify the Action Target IT team and forward them the email at servicedesk@actiontarget.com.
- Provide any details about the incident to the IT team (approx. time, what you entered, screenshots if available)
- Follow the instructions the IT team provides you - this may require additional containment (password resets, account hold, forensic review).
What's the Goal?
This email is trying to trick you into giving up your Action Target login and multi-factor authentication by creating a false emergency — for example, claiming your account will be deleted unless you “verify” right away. If you enter your credentials or MFA code, attackers can take over your account and use it to read sensitive messages, send more phishing emails from a trusted address, request fraudulent payments, or create automatic forwarding rules to keep access.
Attackers rely on pressure and perceived authority (pretending to be IT or a trusted service) so you’ll act without checking. Always pause, verify the request through a different channel (phone or the official IT helpdesk), and report the email to IT if anything seems off.
Takeaway: Attackers rely on urgency and familiar-looking interfaces. Pause and verify every request for credentials or multi-factor authentication via an independent channel. If you suspect compromise, report to the IT team immediately -- fast containment reduces the damage.

No Comments